As recent data breaches show, every organization needs to take action to better secure insider access, particularly that of privileged users and contractors. By Travis Greene, NetIQ, the security portfolio of Micro Focus In 1992 during the preparation for Bill Clinton’s first presidential campaign, political strategist James Carville, in an effort to focus the messaging, hung a sign in the …
Lees verder »When Multi-Factor Authentication Fails
Recently, we’ve seen evidence of the increase in insider threats related to outsiders obtaining and abusing insider credentials. Like others, I’ve pointed to multi-factor authentication (MFA) as a means to mitigate the risk posed by this attack method. But, it’s worth considering – what are the limitations of MFA in reducing the risk of outsiders abusing insider credentials? To be …
Lees verder »Multi-factor Authentication: Waking up to the Elephant in the Room
If the Panama Papers were a wake up call to pay closer attention to insider threats, two recent developments have revealed that we have awakened to an elephant in the room. The first is the release of this year’s Verizon Data Breach Investigations Report (DBIR) on April 26, which states, “63 percent of confirmed data breaches involved weak, default or …
Lees verder »Thar She Blows: Mitigating Whaling Risk
CIO recently reported that a variant of spear phishing called whaling has emerged as a major cybersecurity threat. Whaling is a social-engineering scheme that uses the relationship between executives and employees to trick employees into taking an illicit action. An attacker masquerading as an executive bids, and the employee does his or her bidding. Notable companies such as Snapchat, Seagate, …
Lees verder »Discouraging Attacks from Within
What does the name “Panama Papers” bring to your mind? Outed tax evaders? Exposed grafters? Money launderers? Or like me, does your mind go straight to the risk and prevention of insider security breaches? For those of you who don’t habitually pore over the financial or security press, the Panama Papers refers to a massive and lengthy data breach that …
Lees verder »Understanding Why Business Managers Hate Access Certifications
Almost every job includes monotonous—but necessary—tasks that we dread completing. For line of business (LOB) managers, access certification is one of these tasks. Imagine a seemingly endless list or spreadsheet containing lines upon lines of users’ names coupled with their levels of access. In addition to a long list of other responsibilities, LOB managers are responsible for carefully evaluating whether …
Lees verder »Dynamic Authentication – the New Benchmark
Data breaches have become commonplace these days, and enterprises around the world agree that it’s not a matter of “if” but rather “when.” Complicating matters, gone are the days when your employees worked nine to five, from their desktops or laptops, or even within the walls of the office where access is delivered in a predictable, simple and easy to …
Lees verder »7 lessen in social media voor crisisbeheersing voor hulpverleners of evenementenorganisators
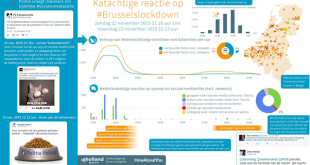
Een brand, noodweer of flinke crisis staat binnen enkele minuten op social media. Dat kan lastig zijn voor de crisisbeheersing door hulpverleners of evenementenorganisators. Maar deze berichten op social media geven achteraf ook een inkijk in de beleving van de crisis en hoe deze zich ontwikkelde. Kritieke momenten Onderzoekers van HowAboutYou (partner van het congres Veiligheid bij Evenementen), Infopunt Veiligheid én het …
Lees verder »Signaleren van online sporen van radicaliserende personen
Tijdens de aanslag op de luchthaven Zaventem en het metrostation (maart 2016) verschenen binnen 12 uur meer dan één miljoen (!) Nederlandstalige berichten op sociale media en nieuwsmedia. Op sociale media en nieuwsmedia zag je observaties, hulpvragen, uitingen van medeleven en afschuw, statements van politici, verslaggeving door nieuwsmedia, spontane burgerhulp, feiten, fouten en mythen. Kip of ei? Zorgde het bereik …
Lees verder »Betere beveiliging mobiele data en apparatuur
Minder dan een op de vijf Nederlanders heeft zijn smartphone, laptop of tablet zodanig beveiligd dat hij zijn mobiele apparatuur bij diefstal onbruikbaar kan maken. Hierdoor loopt ruim 80% van de Nederlanders het risico dat persoonlijke gegevens na diefstal op straat belanden. Daarom roept minister Van der Steur (Veiligheid en Justitie) Nederlanders op hun mobiele apparaat ‘Boefproof’ te maken. Ook …
Lees verder » SBO Blog Het blog van Studiecentrum voor Bedrijf en Overheid
SBO Blog Het blog van Studiecentrum voor Bedrijf en Overheid